
Charter of Trust – Secure Development Lifecycle: step-by-step guidelines
As 2023 marks the fifth anniversary of the Charter of Trust, we are publishing a “Secure Development Lifecycle: step-by-by step guidelines", our latest guiding document in line with the Charter's Principle 3, Security By Default.
Read more
February 15, 2023
• 5 min read


Invitation to the Charter of Trust 5th anniversary event at the Munich Security Conference 2023
The Charter of Trust is pleased to invite you to its 5th anniversary event, as part of the Munich Security Conference 2023, which will take place both in-person in Munich and virtually and gather Charter of Trust Partners and cybersecurity experts.
Read more
January 19, 2023
• 5 min read


CoT welcomes new Associated Partner CSA
The Charter of Trust is pleased to welcome the Cloud Security Alliance (CSA) to its Associated Partner Forum (APF).
Read more
January 09, 2023
• 5 min read


Principle Use Cases – AES
How can companies increase the cybersecurity awareness of their employees? AES shares their take on implementing new and innovative training model that drives engagement.
Read more
January 03, 2023
• 4 min read


CoT welcomes new Associated Partner CSIR
The Charter of Trust is pleased to welcome South Africa’s Council for Scientific and Industrial Research (CSIR) to its Associated Partner Forum (APF).
Read more
December 19, 2023
• 5 min read


Principle Use Cases – IBM
How can companies ramp up their cybersecurity capacities and upgrade skills to provide a confident response to incidents? IBM shares their take on how they trained their customers to be proactive responders in a new Charter of Trust Principle Use Case.
Read more
December 13, 2022
• 4 min read


Principle Use Cases – Mitsubishi
How can companies cooperate to improve their supply chain security? Mitsubishi shares their take on developing a joint approach among partners to establish common cybersecurity awareness practices in a new Chater of Trust Principle Use Case.
Read more
December 06, 2022
• 5 min read
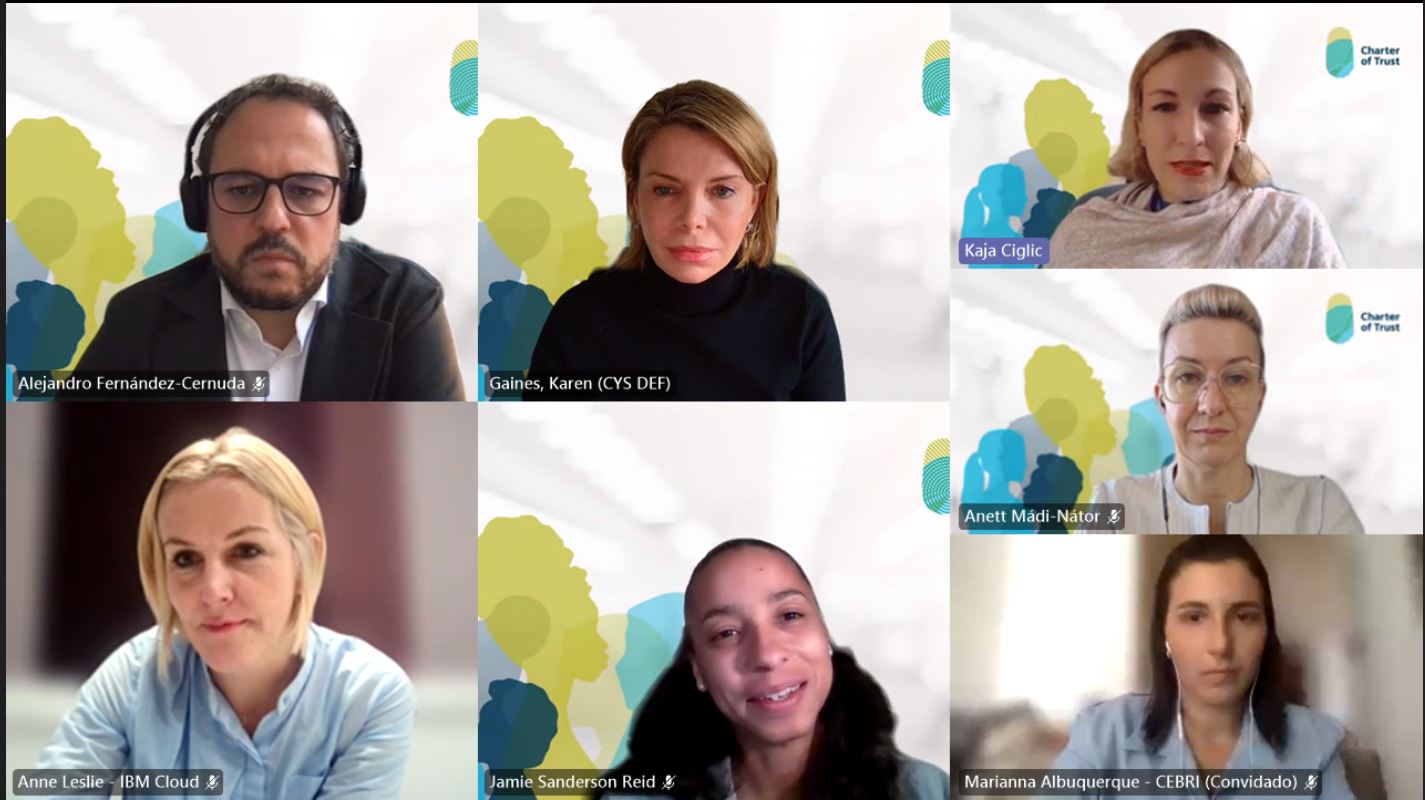

Women in Cybersecurity Workshop
On 21st November, the Charter of Trust hosted a virtual workshop with three key sessions on the topic of 'Women in Cybersecurity' and how to build DEI&C awareness, capability and competence across communities, counting with high-level speakers from the public and private sectors.
Read more
November 22, 2022
• 4 min read


Principle Use Cases – Atos
What are the main challenges and opportunities of Threat Intelligence sharing? Atos shares their take on bringing together experts from various partners and why this is a smart move.
Read more
November 22, 2022
• 3 min read
Principle Use Cases – Bosch
What approach can businesses take to resolving problems concerning Artificial Intelligence? Bosch details their experience based on the VCIO approach. Learn more in their Principle Use Case.
Read more
November 16, 2022
• 4 min read


Microsoft joins Charter of Trust for greater cybersecurity collaboration
Microsoft has joined the Charter of Trust (CoT) cybersecurity initiative as of November 10, 2022. As a CoT member, Microsoft plans to contribute its cybersecurity expertise in developing and promoting awareness of robust security principles for a secure digital world. With the addition of Microsoft, the Charter of Trust initiative has grown to 18 members.
Read more
November 10, 2022
• 5 min read


Principle Use Cases – Allianz
How to keep employees aware of cyber risks and up-to-date with how to self-protect against cyber-attacks? Learn from Allianz as they share their best practices in a #UseCase under Charter Of Trust principle 6 "Education".
Read more
November 09, 2022
• 4 min read

 PUBLICATIONS
PUBLICATIONS EVENTS
EVENTS NEWS
NEWS


